Security of your information is our primary concern
Ensuring that your confidential and sensitive information is protected at all times is one of our most important concerns.

Data Security
Passwords
The system enforces strong passwords that may include characters, digits, special characters etc. It is up to the user to ensure that the confidentiality of the password, and user ID is maintained. When combined with Multi-Factor Authentication, it provides for extremely secure access to the system. No employees or administrators will have access to this information and you should change passwords on a regular basis. Should you forget your user ID or password, you can use the system’s Forgot Password feature to reset it.
Encryption
All data is encrypted, at rest, using AES-256 with a public key to encrypt data and a private key to decrypt it. Each user will have a unique key. All data communication is also encrypted, in transit, using HTTPS with SSL/TLS with a 2048 to 4096-bit certificate to determine the public key size.

Data Sovereignty
Protecting Your Privacy Across Borders
Data sovereignty refers to the concept that digital information is subject to the laws of the country in which it is located. This means that the privacy and security of your data are governed by the regulations of the country where it is stored. Data sovereignty impacts your privacy, security, and legal rights. Different countries have varying laws regarding data access, storage, and protection. Ensuring your data is managed in compliance with local laws can protect you from unauthorized access and misuse.
Inheritus complies with international data protection standards, such as GDPR in Europe, PIPEDA in Canada, CCPA in California and more. International users’ data are automatically stored in locations to ensure compliance with local regulations.
Operations
We are guided by industry best practices and follow them in order to protect your sensitive and confidential data and documents. These practices include software vulnerability testing, intrusion detection and cyber security audits. Critical software updates and patches are provided immediately on an as-required basis by our systems personnel.
Our online environments are provided by world-class service providers such as Amazon, Google and Microsoft. These environments are monitored on an ongoing basis for security issues and all updates, fixes and patches are applied as required.


Role Based Access Control
The software uses Role-Based Access Control to allow access to certain features and functions by the role of the individual accessing the system. This control maintains confidentiality of your sensitive data and documents and restricts access to only those persons you would like to have access using cryptography such as SHA-256. Employees or administrators can only access non-sensitive data in order to provide support and assistance to users.
The system uses an invitation-only approach to document sharing with Trusted Advisors, Estate Trustees and other contacts and this sharing can be started and terminated at anytime depending upon the needs of the user.
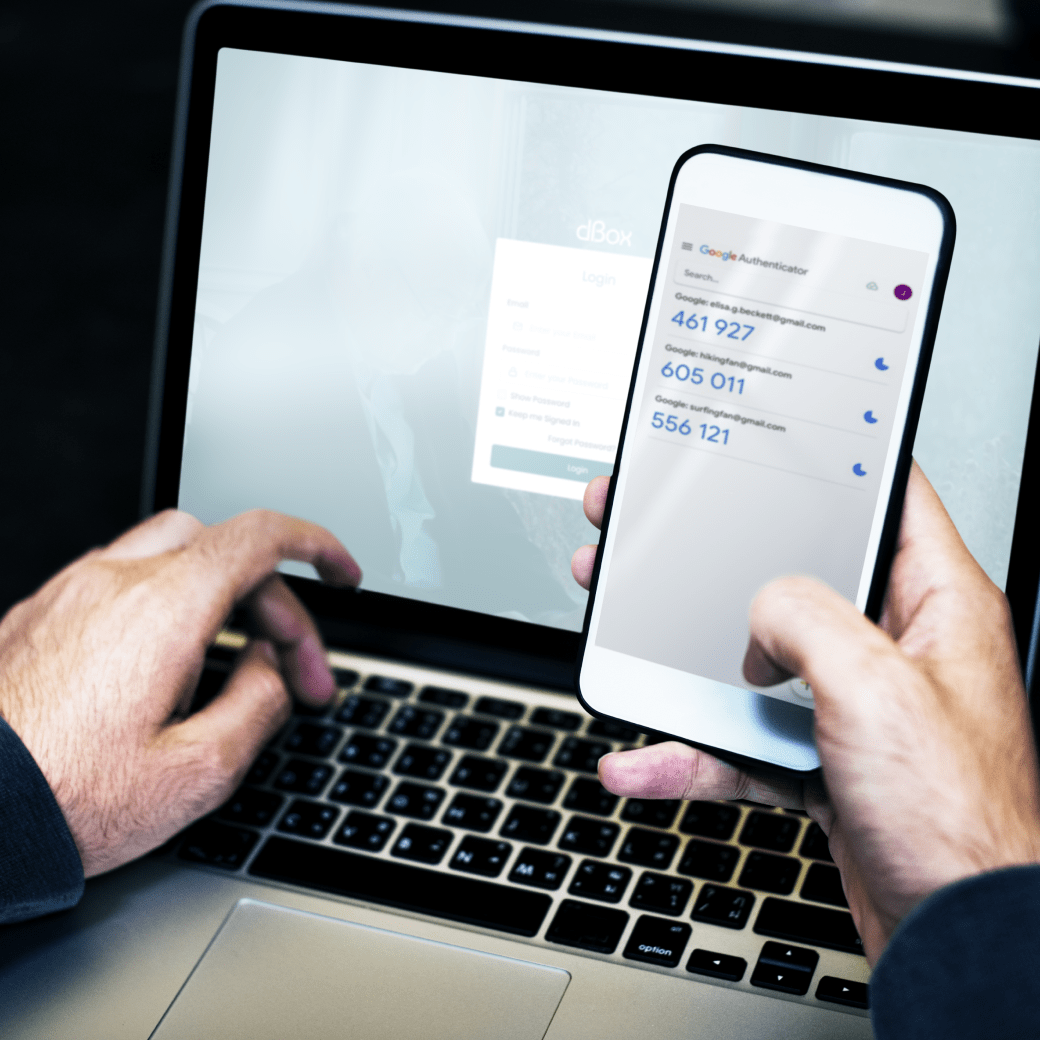
Multi-Factor Authentication
Multi-Factor Authentication (MFA) or Two Factor Authentication allows you to add an additional layer of security to your data and use of the system. You can use the Google or Microsoft Authenticator Apps or request a secure code to be sent to you via email or SMS Text Message. Use this code in conjunction with your login credentials to securely access the system. Should your password be lost or compromised, no one will be able to access your account since you’ll be the only person with the secure code required for successful access.
Each time your account is accessed or a password is changed, you will be notified and the system tracks all usage for auditing and reporting.

Standards Compliance
- PIPEDA (Canada)
- Freedom of Information and Protection of Privacy Act (Regional)
- GDPR (European Union)
- HIPPA (USA)
- Safe Harbor Privacy Principles
- TBS Guardrails & Government of Canada Security Control Profile
- ISO 27001:2005
- ISO 27002 and ISO 27005
- SOC 1 and 2 Type II
Measurement & Reporting
We use standardized compliance techniques in conjunction with our Auditors. We identify and assess compliance issues based on our policies and procedures and analyze our risk and exposure. We follow-up and do compliance gap analysis and evaluate best practices for risk mitigation. Finally, we fix identified issues and continually monitor to ensure that there are no repeating issues.
Our security features include
Leading-edge security technology, data and analytics tools
Strong internal controls like firewalls and email security software
Managing security threats 24/7/365
Mandatory employee training on Cybersecurity practices

Need More Details? Lets Connect!
Our Sales team can help with reliable and accurate answers to your questions and concerns.